Open-source tools play a pivotal role in securing the software supply chain. These tools are developed and maintained by a community of contributors and are available for anyone to use, modify, and distribute. The transparent nature of open-source software enables a broad base of users to inspect, improve, and validate the security of these tools.
Similarly, open-source tools often lead the way in innovation and security practices. The collaborative environment encourages rapid development and the sharing of best practices. This often results in quickly identifying and patching vulnerabilities, outpacing proprietary software in responsiveness. Additionally, using open-source tools in the software supply chain promotes standardization and interoperability, making it easier for different systems and applications to work together securely.

Key Open-Source Tools for Software Supply Chain Security
Let’s now dive deeper into vital open-source tools for supply chain security.
1. Dependency trackers and scanners. Tools like OWASP Dependency-Check help identify known vulnerabilities in software dependencies. These tools scan project dependencies against a database of known vulnerabilities and provide insights on how to mitigate potential risks.
2. Static code analysis tools. Tools such as SonarQube and ESLint enable developers to automatically review code for potential security flaws. They can detect issues like buffer overflows, SQL injection vulnerabilities, and other common security pitfalls in code.
3. Dynamic application security testing (DAST) tools. DAST tools, like OWASP ZAP and W3AF, are used to find vulnerabilities in running web applications. They simulate attacks on web applications and identify weaknesses like cross-site scripting and insecure server configurations.
4. Software composition analysis (SCA) tools. These tools efficiently detect open-source components and their corresponding licenses within a codebase. They are adept at highlighting possible license compliance concerns and alerting developers about recognized vulnerabilities in these components. Tools such as FOSSA and WhiteSource help manage open-source license compliance and security.
5. Container security tools. With the rise of containerized applications, tools like Clair and Docker Bench for Security are essential. They scan container images for vulnerabilities and provide best practices for securing containerized environments.
6. Continuous integration/continuous deployment (CI/CD) security tools. CI/CD pipelines not only compile and test new code to ensure functionality and compatibility but also, with DevSecOps, enforce security practices pre-merge and pre-deployment. Shift-left security emphasizes early developer involvement in security, while CI/CD offers essential automation for upholding security standards in both infrastructure and applications.
7. Secret management tools. Managing secrets like API keys and credentials securely is vital. HashiCorp Vault and Mozilla SOPS provide mechanisms to securely store, access, and manage sensitive information.
8. Infrastructure as code (IaC) scanning tools. As infrastructure becomes more code-defined, tools like Terraform and Ansible need security scanning. Checkov and Terrascan are IaC scanning tools that help identify misconfigurations and enforce security best practices.
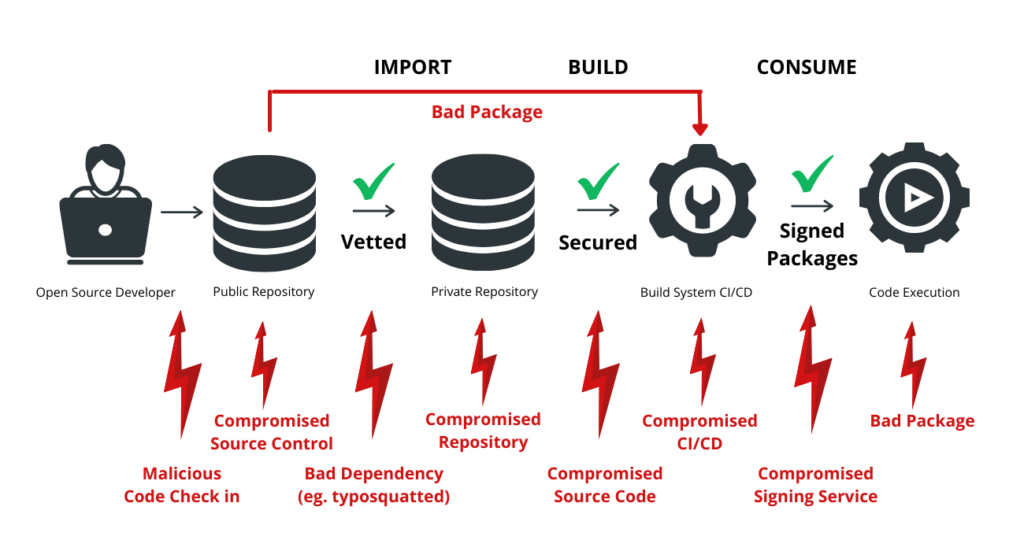
Challenges and Risks
Open-source software has evolved considerably from its early days, such as with the emergence of Linux, which initially aimed to democratize software and provide a free alternative to costly proprietary options. While open-source software offers numerous advantages, it now also presents more significant inherent risks.
Incorporating open-source software into the software supply chain poses notable concerns regarding introducing vulnerabilities into systems. One contributing factor to these vulnerabilities is that open-source projects often rely on a limited number of contributors. Additionally, the extensive size of open-source packages can render it practically impossible to thoroughly inspect every component, making it challenging to effectively identify and address security vulnerabilities.
The intrinsic risks associated with open-source software underscore the importance of implementing a robust software supply chain security strategy to safeguard against potential threats. Offering significant advantages, open-source tools come with challenges. One primary concern is the reliance on community support for updates and patches, which might not be as prompt as commercial solutions.
Best Practices for Implementing Open-Source Security Tools
Let’s now delve deeper into the specifics of implementing open-source security tools, exploring effective strategies for vulnerability scanning, CI/CD pipeline integration, regular updates, community engagement, and team training to enhance software security.
1. Regular vulnerability scanning. Incorporate regular scans at different stages of the development lifecycle to identify and remediate vulnerabilities early.
2. Integrate security into the CI/CD pipeline. Automate security checks within the CI/CD pipeline to ensure continuous security assessment.
3. Stay updated. Keep all tools and their dependencies updated to the latest versions to protect against known vulnerabilities.
4. Community engagement. Participate in the open-source community to stay informed about the latest security updates and practices.
5. Training and awareness. Educate the development team about best practices using these tools and the importance of software supply chain security.
Conclusion
Open-source tools offer powerful, flexible, and cost-effective solutions to enhance supply chain security.
However, it’s important to approach their integration with a strategy that encompasses regular updates, community engagement, and comprehensive security practices. By leveraging these tools effectively, organizations can significantly bolster their defense against the increasing threats targeting software supply chains.